Top Secret is now released! This has been a long journey and I want to thank everyone who backed the game and made it possible.
So without further ado, thanks and enjoy the game.
James
| Release | |
| Rewards |
Top Secret is now released! This has been a long journey and I want to thank everyone who backed the game and made it possible.
So without further ado, thanks and enjoy the game.
James
I’ve just added support for email attachments in Top Secret. The earth shatteringly obvious feature was something I’ve long wanted to do but had never quite got round to. Many of the Snowden docs have been released in PDF format and now they’ll be working their way into the game. In fact, it was the release of some documents very recently that spurred me into action…
A few weeks ago, The Intercept released excerpts from the NSA’s internal staff magazine ‘SID Today’. Banal yet fascinating, these documents reveal both the human and organisational culture behind NSA. There’s stuff about recruitment and promotions, staff events, jokes and morale-boosting missives. In short, it’s fantastic at emphasizing that the people working there are just regular folk working in conditions not too far removed from your own. This is the ‘banality of evil’ in today’s world. Normal, nice people working hard for an organisation which breaches human rights worldwide. There’s no malice, no evil men in suits, just people doing their job.
Every day in Top Secret, you’ll receive a new edition of SID Today into your inbox, but if you want to take a look right now, you can read more about them directly here.
Last week, Google announced their new smartphone messaging app Allo. Should you use it?
Answer: No.
Let me explain why.
One of the best ways of resisting mass surveillance is to use services where end-to-end encryption (E2EE) is enabled by default. E2EE means that only the sender and receiver of a message can read it. The NSA could still read messages by hacking into your phone directly, but they can’t (unless they hack everyone’s phones) read everyone’s messages this way. This is why widespread adoption of services such as WhatsApp (which uses E2EE) is a good thing.
With WhatsApp, iMessage, and Signal adopting E2EE by default, many were looking to see what Google would do with their latest product. Would they also use E2EE?
Well… sort of.
Allo only uses end-to-end encryption in ‘Incognito mode’. By default, messages are not encrypted this way. Furthermore, incognito messages are only stored for a few minutes. While good for security, this disincentivises continuous use of the mode. The likely result? The vast majority of Allo messages will not be securely encrypted. Google, and governments worldwide will be able to read, and analyse the messages of everyone using the service. This is a bad thing.
So which messaging service should you use if you care about human rights? To answer this question we have to briefly talk about metadata.
E2EE protects the contents of messages but not the metadata (who, what, where, when) of the parties involved. Metadata is just as important (if not more so) than content when it comes to mass surveillance - it’s easy to analyse in bulk and can be used to determine the important places, people, and daily patterns in your life. A good messaging app should protect not only the content of your communications but also the metadata.
WhatsApp uses E2EE but hasn’t said whether it stores metadata. Given that its terms explicitly allow for metadata collection we should assume that it does. iMessage also stores metadata. So what’s the alternative?
The general consensus right now seems to be that Signal is the best option. It uses E2EE by default and doesn’t store any metadata. It has clients for Android, iOS, and desktop and is a joy to use. Unlike WhatsApp, Signal is completely open source so anyone can check the code for security flaws or malicious behaviour. What’s more the tech behind Signal is so widely respected that both WhatsApp and Google have adopted it.
But don’t just take my word for it. Signal is recommended by, among others, himself.
You can download Signal here.
James
I’ve recently added a new feature called SEARCHLIGHT to the game.
SEARCHLIGHT allows the player to find out more about SIGINT, infosec, TIDE, PGP, and TOR. And if that sounded like a load of gobbledygook to you then don’t worry, that’s exactly why I created SEARCHLIGHT in the first place!
In Top Secret, SEARCHLIGHT is the NSA’s in-house tool for jargon busting. You can think of it like a simple command line interface via email. Whenever the game uses an acronym or refers to subjects you aren’t familiar with, you can use it to find out more. For example, you can email SEARCHLIGHT queries such as:
DEFINE encryption
or
DEFINE SIGINT
and it will send back descriptions of those topics.
You can also query for ongoing NSA operations and programs (real or from the game). E.g.
PROGRAM PRISM
or
PROGRAM SEARCHLIGHT
But be careful! Querying operations above your clearance level, or ones you shouldn’t know about may have repercussions…
Normally, between Kickstarter updates, I make a note of every interesting article about Snowden, privacy, and surveillance issues I come across. This list is then ruthlessly whittled down to a final select few which make up the In the news section of the update. In a typical two week period I record about ten relevant news stories. This fortnight my list runs to over fifty!
And so we must talk about Apple. And why they don’t want to help the FBI unlock a terrorist’s phone.
If you’ve missed the news, Apple is currently fighting a legal case against the FBI over whether or not they should aid the FBI in unlocking an iPhone which belonged Syed Farook, one of the San Bernardino shooters. The FBI want Apple to write code which makes it easier for them to break the password on the phone.
It sounds simple and reasonable. Why not help?
Apple have two main objections:
Apple fears a future where they’ll have to write versions of iOS to spy on their customers for governments. If the US demands this capability, why not other countries? If the exploit exists, how can we stop Russia using it to break into the phone of a gay activist, or China using it on an iPhone belonging to pro-democracy protesters?
For its part, the FBI says that the case ‘isn’t about trying to set a precedent’ although in typical obfuscatory style it gives the impression of addressing Apple’s points when it doesn’t. In particular it doesn’t refute the fact that a precedent would be set, or that the exploit could be reused in other cases.
It’s hard to tell what will happen at this stage. Apple can afford good lawyers and it’s possible the case could go all the way to the supreme court. The wider context is worth examining though.
Firstly the case can be seen as a major battle in what is being called ‘the second crypto war’. Questions last debated in the ‘90s have resurfaced post-Snowden. Should it be legal to provide encryption which even the government can’t break? Companies such as Apple have been working to improve the security of their products and governments are worried. If end-to-end encryption becomes widespread, the ability of the NSA and GCHQ to mass surveil is reduced.
Secondly, why Apple? Where are Facebook, Google, Microsoft in this fight? Unlike their competitors, Apple has a unique combination of custom hardware/software, a business model not predicated on customer surveillance, and huge resources to challenge the government. It also, in Tim Cook, has a man who respects and understands the need for privacy. As a minority, he knows that keeping a secret, having privacy, is all that keeps many people safe from unjust persecution. It’s not a coincidence that two of the strongest privacy advocates, and the first two people Snowden reached out to, Glenn Greenwald and Laura Poitras, are also members of the LGBT community. That’s not to say gay people have a monopoly on this subject (far from it), but It’s certainly easier to value other people’s’ privacy when you would have been jailed a generation ago if not for yours.
I don’t want to let Apple off scot-free. All of their software is closed-source and a great deal of what they say has to be taken on trust. I don’t think that closed-source software is the best way to guarantee privacy and security, but it’s great to see a silicon valley giant take such a big stand on this important issue. It’s just a shame that it’s taken a corporation, rather than elected officials, to stand up for our rights.
Over the last two weeks I’ve been working on the offline version of Top Secret. The ‘offline version’ allows you to play without an internet connection and every purchase of Top Secret comes with an offline copy!
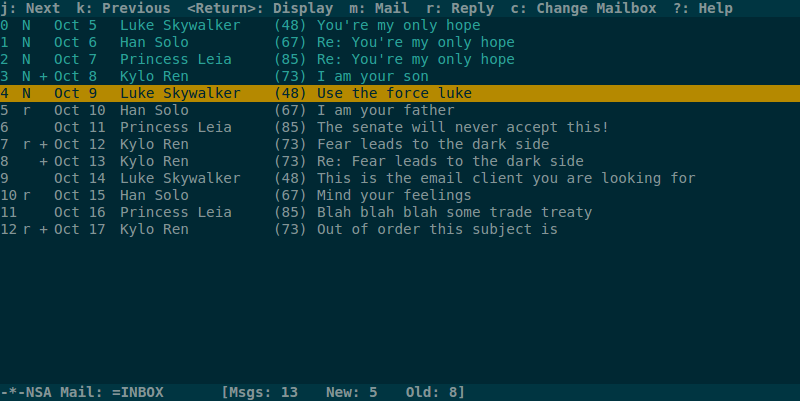
What does a Top Secret NSA email client look like?
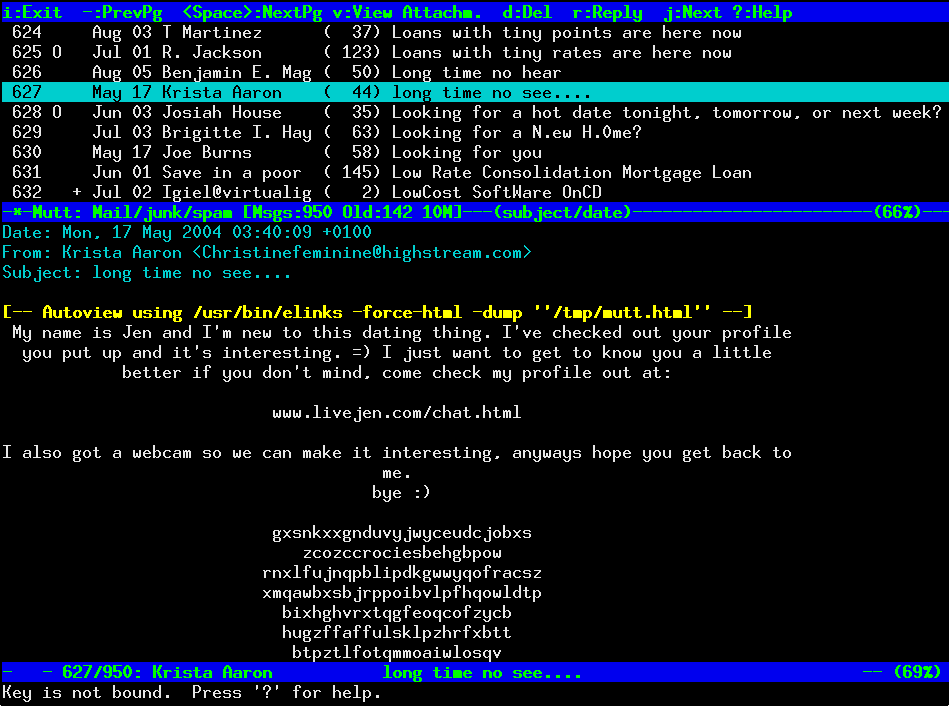 All mail clients suck. This one just sucks less. - Mutt slogan
All mail clients suck. This one just sucks less. - Mutt slogan
Mutt is a text-based email client made in 1995. Despite its age and minimal UI, it’s still used today by security conscious people such as Christopher Soghoian, Principal Technologist at the ACLU. It might be ugly, but the small codebase, and the fact it doesn’t run in the browser make it harder for adversaries to attack you via email.
The offline version of Top Secret is designed to be a (much!) simpler version of Mutt. It’s completely keyboard controlled and supports many of the same key bindings as Mutt. Take a look!
ps. I’ve been playing around with colour schemes. Let me know which one is your favourite in the forum.
 Black and white - for the chromaphobes
Black and white - for the chromaphobes
 Black and blue - dash of colour
Black and blue - dash of colour
 Green - real hackers use green text
Green - real hackers use green text
 Solarized - the One True Colour Scheme
Solarized - the One True Colour Scheme

Last Thursday I attended Scrambling for Safety, a conference about the upcoming UK surveillance law the Investigatory Powers Bill (IPB). The event drew participants from parliament, the media, NGOs and even the security services, including David Omand, the former head of GCHQ. Here’s my take on what was discussed.
Context: Following the Snowden revelations, several reviews were instigated into surveillance laws and capabilities in the UK. The findings? Current UK laws on surveillance were outdated, unclear, and, in the words of the Independent Reviewer of Terrorism Legislation, David Anderson, ‘undemocratic and intolerable’. The last major UK bill on the matter (RIPA) was passed back in 2000, before Facebook and Twitter existed. Everyone agrees it’s time for new legislation. Enter the Investigatory Powers Bill.
Unusually for a western nation, UK intercept warrants are signed by politicians rather than judges. There has been a lot of pressure on the government to change this but the IPB proposes a compromise via a so-called ‘double-lock’ mechanism. Ministers will still sign warrants, but they will be subject to judicial review. The key controversy here is what form that review will take. Will it merely check that the correct procedure was followed, or will it evaluate the proportionality and legality of each warrant?
These include mass data held by companies and public organisations which are not classified as ‘communications data’. E.g. Google calendar data for everyone in the country, Oyster card records for every journey made in London, or medical data on (hundreds of) millions of people. The IPB proposes that GCHQ can demand companies and public bodies provide such info. They cannot refuse. How these data sets are analysed and used is unclear.
This includes programs revealed by Snowden such as Tempora which copies virtually all internet traffic going in and out of the UK directly from the fibre-optic internet cables. The bill aims to legalise these programs. The key contention here is whether storing data is itself a threat to privacy and security. The security services and government say that they will store everything but only look at data for which they have a warrant. They’re effectively putting surveillance cameras in every room of your house but promising ‘we won’t look at the footage, trust us’.
Both of which relate to bulk collection. Judicial privilege is the idea that clients and their legal advisors should be able to communicate in confidence. This is a critical part of a well-functioning justice system. How can we reconcile this with programs that store client-attorney communications such as those legitimised by the IPB? Once again the argument is made that as long as the emails, calls, and messages are only stored and not read, legal privilege is preserved. Will a torture victim taking a sensitive human rights case against the government feel the same? That it’s ok for the government to hold a copy of private emails they’ve sent to their legal team? I’m not so sure.
The same principles apply to journalists and their sources.
The question that won’t go away. In particular: Can you setup and run a communications company offering secure, end-to-end encryption in the UK? i.e. a service where you cannot read or access the content of the communications, and where the law cannot compel you to modify your software/hardware to do so. Home Secretary Theresa May has been especially slippery on this issue, and exceptionally careful in her use of language. She doesn’t seem to have answered this exact question and will need to do so before the bill.
Most communication and software services are international and cross multiple jurisdictions. What happens if a company is required to give up data by UK law, but forbidden by the jurisdiction where the data is held? The IPB makes extra-territorial requests of companies but offers no concessions to solve this issue. Facebook and others are worried. Markets may be global but, according to the government, human rights aren’t.
Aka ‘hacking’. In particular, hacking of innocent people’s machines, and of critical infrastructure. With interconnected devices, it can be hard to evaluate all associated risks, and with the ‘internet of things’ this will only become more difficult in the future. This also highlights the unusual duality of GCHQ, parts of which are protecting our companies from cyber attacks, whilst other departments are attacking those same companies and leaving them open to attacks from others.
Laws take a long time to change, technology doesn’t. In an effort to keep apace with technological changes we have seen security services act, and ask for permission later. How can we reconcile this with the needs of democratic accountability and transparency? Is there a better way than having the law simply catch up with GCHQ’s capabilities every decade? Perhaps, but government isn’t offering one.
Perhaps the biggest problem of all. The draft bill is a hugely complex 300 page long, inscrutable behemoth. It’s clear that virtually no one understands the full contents or implications. Especially not MPs. Keir Starmer (who speaks for Labour on the issue) spoke at the conference but despite vague references to ‘protecting privacy while giving the security services the powers they need’, didn’t display a firm grasp of the bill. Given that NGOs, multinationals, and dedicated journalists are struggling to understand the proposals, it’s not surprising that busy MPs don’t, but it’s worrying nonetheless.
Attending Scrambling for Safety, it’s clear that the gap between the government and human rights campaigners on this issue has not narrowed. The government’s response to the Snowden leaks has simply been to try and place everything revealed into statute. The IPB doesn’t have to be a bad thing. Increased transparency and oversight are long overdue. Unfortunately the draft bill will, for the first time, explicitly place mass surveillance into law in the UK.
The good news is that there’s still time to stop that happening.
NB. This is not a tech article. If you’re interested in the how the editor was made have a look at the and keep an eye out for a more technical blog post which I’ll be writing soon.
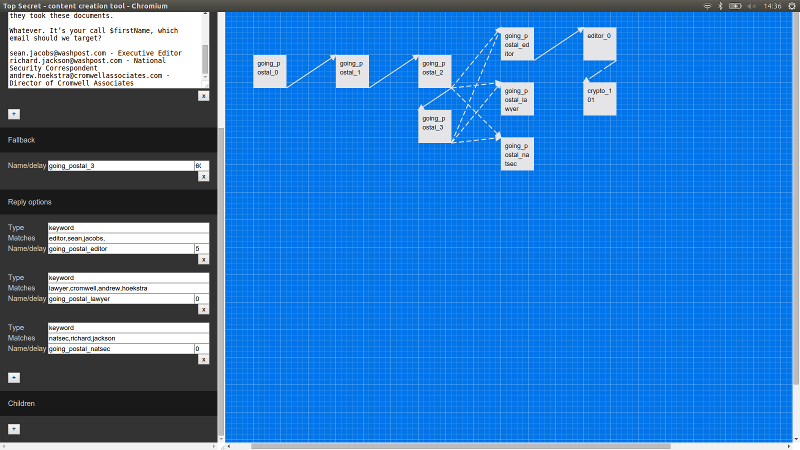 The new editor
The new editor
The editor is split into two parts, the side panel and the content area. The side panel (left) is used to edit the currently selected message(s), and the content area (right) shows each message and how they connect to other messages.
Each box in the content area represents a single email in the game. They all have a name, subject, from, to, and body. They also contain information describing how they connect to other emails - not only which email(s) to send next, but under which conditions, and after what time delay. This is where the magic happens, how a set of disparate emails are combined into an interactive experience!
The data describing the connections are represented by a message’s fallback, reply options, and children.
Fallbacks describe the next message to be sent if no replies are received by a certain time (or if replies are not supported for this email). The fallback describes not only the next email to send but how long to wait before sending it.
Reply options allow branching based on a player choice. They allow you to specify a different response if, for example, the player replies ‘yes’ or ‘no’.
Children allow the game to spawn multiple concurrent email threads. Each child starts a new thread in parallel to the current one. This allows the narrative to not only branch but to have multiple branches alive all at once.
All together these provide a way for Top Secret’s narrative to be:
Ok, let’s use our new arsenal to understand our original thread:
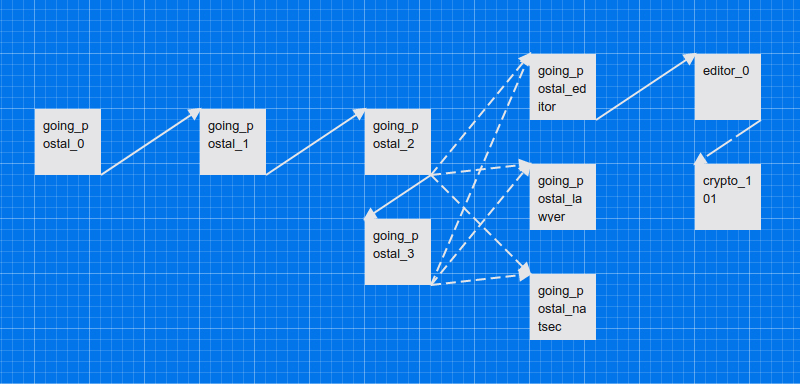
A sample thread showing emails (boxes), fallbacks (solid arrows), reply options (dashed arrows), and children (partially dashed arrows)
From left to right the first few emails (from going_postal_0) take place sequentially, and unconditionally using fallbacks. At going_postal_2 the player is presented with a three-way choice. If they don’t reply in time the fallback kicks in and they are sent to going_postal_3 which gives them the same identical choices and another bite at the apple. One of the choices leads to a new thread editor, and this also begins a new child thread crypto 101 in parallel.
Phew!
Ok, that probably sounds a bit confusing and complicated. Imagine trying to hold all these connections in your head or on a piece of paper - now you understand why the visual editor is so useful.
Not only is the new editor easier, and quicker to use than the previous one, it also allows you to see unconnected messages and errors instantly.
The editor is still a work in progress and I’ll be tweaking it as I go along. If you have any cool ideas, or thoughts on the implementation let me know.
Thanks for reading!

Due to demand, I’m reopening three Kickstarter reward tiers for a limited time only. Grab the CONFIDENTIAL, SECRET, and TOP SECRET tiers now!
This is your last chance to get:
See the available tiers HERE.
Yes, yes, I know, crowdfunding postmortems are ten a penny. Everyone makes the same mistakes and then describes in detail how you can avoid them.
Planning. Marketing. Funding graph image. Check, check, check.
This one will be different! Read on to find out some things you might not know about Kickstarter campaigns…
Games journalists don’t care about your Kickstarter. Your campaign is NOT an interesting story for them. The only exceptions to this are if:
Neither of which is much help to most indie devs. But even though they don’t care about your campaign, they might care about your game.
Here the usual rules apply. If your game is unique, and resonates with their audience, you have a good chance of getting coverage. Uniqueness is key. What makes your game different?
Top Secret had 3 main hooks:
Press covered the game purely because of the above. I’d go as far to say that it didn’t matter what the game was, or how it played. Some journalists covered it simply because they cared about surveillance issues.

As a Brit (Chris Roberts excepted), I found this especially difficult.
In an ideal world, all your backers would be people you’ve never met who are completely in love with your product. In reality, if you’re running a small indie campaign, it’s likely that at least some of your campaign funds will come from people you already know.
You will have to spam Facebook/Twitter with Kickstarter news. You will have to chase up with people to see if they’ll back. In particular, you’ll need family and friends to boost the campaign in the first 48 hours.
This will all feel terribly awkward but you should do it anyway.
ps. Keep track of which friends have backed before you go to a social gathering. Thanking a friend for backing when they haven’t, or not thanking someone for backing because you’re not sure if they have, are both big no-nos. Trust me.
“Your campaign is killing it!”
“Kick things up a notch!”
“Regarding FOX news interview for Top Secret”
Prepare to be blitzed by “Crowdfunding consultancies” and “Crowdfunding PR experts”. They’ll promise you GUARANTEED news coverage in X news sites, and a MINIMUM of Y retweets seen by Z people.
My advice is to ignore these emails. Maybe they work, maybe they don’t. It’s just so difficult to sift the wheat from the chaff. I’m guessing they make a lot of quick money from people running failing campaigns who get desperate. Marketing IS important, but throwing money at the problem won’t help.
On a semi-related note, think about how you’ll manage your communications. My inbox filled up rapidly during the campaign and it was hard to keep track of who I had and hadn’t replied to.

Kickstarter campaigns are all or nothing. Success, or failure. And mostly failure*.
* less than a 1/3rd of game campaigns are successful https://www.kickstarter.com/help/stats.
If you’re especially well-prepared and lucky, your project will lift off and shoot over your target, but most projects aren’t like this. Most are a hard, long, slog, without a happy ending.
It’s also public. If you fail, all your friends and family are going to know. And if you do succeed, you’ll have to deal with the responsibility of keeping all those backers happy.
Naturally this is stressful.
Make sure you have a support network around you. This is especially true if you’re a solo creator. Try not to be snappy or irritable, and realise that people aren’t thinking about the campaign quite as much as you are.
And don’t burn yourself out. Most Kickstarter creators take a few days off after a campaign. There’s a good reason for this!
If you’re stressed, remember this: people want you to help you.
Nothing prepared me for the kindness I received from strangers. People who emailed me about bugs, or broken hyperlinks. Backers who shared and tweeted. People who just wanted to help in any way. I was even invited to play a board game with a backer!
And of course Failbetter have been amazing in incubating the project and supporting the Kickstarter.
A crowdfunding campaign is a weirdly brilliant way of meeting new people and making new friends. Even if your campaign fails, you’ll be richer for the experience.
You’d think, given the name, that the development of Top Secret would be a furtive, clandestine process. A black box where Kickstarter money is put in and a game pops out. Nothing could be further from the truth!
Top Secret will use an open development model. I want you to know what I’m doing, and how the project is progressing right up to release.
What does this mean in practice?
This is where we can discuss game ideas related to Top Secret, and talk directly with each other. An empty forum is no fun, so get involved and start posting!
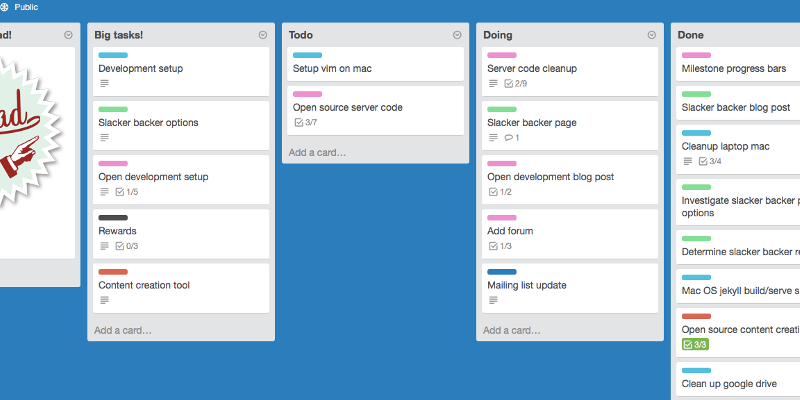
If you want to know what I’m up to right now take a look at the Top Secret Trello board. This shows current/upcoming tasks and describes the current milestones.
If you’re a developer or just interested in the game tech, keep an eye on the open source repositories on . They’re new and empty at the moment, but I’ll start transitioning code across next week. Bug reports and code reviews are encouraged!
If you look at the development blog, you’ll notice there are now progress bars. These give you a quick overview of the current milestones and how close to completion they are. Click on them to take you to the corresponding Trello task.
A mix of development updates as well as general musings on surveillance issues. Take a look here.
Every two weeks on Friday you’ll receive a progress report describing what I’ve been up to and how the game is progressing.
Why am I doing all this?
Hopefully you find the blogs, forums, and code interesting, but I also think it will result in a better game. If you’re engaged in the process, you’re more likely to give me feedback, and cool ideas. Having the code open source means other developers can spot bugs and give me technical advice.
Finally, there’s a saying in the security industry: trust, but verify. You’ve already trusted me, now you can start to verify.
James
ps. Don’t forget to sign up to the forum. I’d love to hear your thoughts on open development.
Wow. At times I wasn’t sure if we were gonna make it, but last night Top Secret reached 100%!
Here’s how it happened:
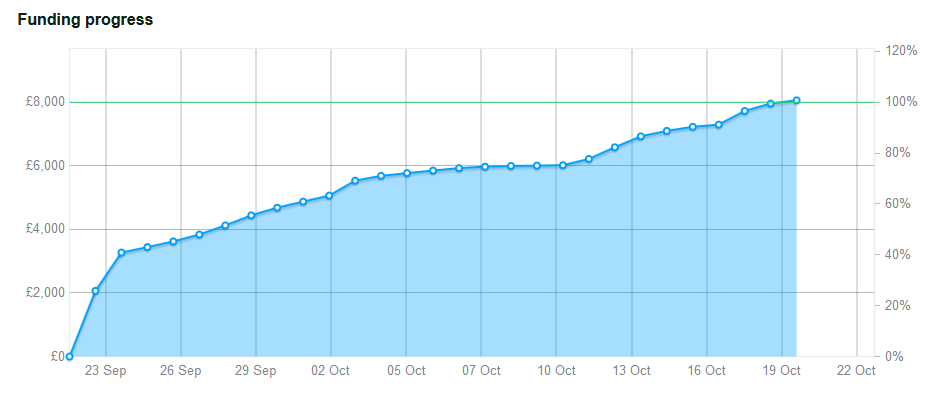
I’ve been constantly amazed by the generosity of friends and strangers alike. Every time the graph started to level out, new backers appeared to keep the momentum up.
You really are marvellous people.
Top Secret is an unusual game. It’s the kind of project that could only happen via Kickstarter, and only with your support. Thank you for taking a chance on it!
The sun is out. Sails unfurled. Our journey has just begun.
James

Game developers often talk about ‘design pillars’. Foundations, the unique combination of which defines a game, these act as a roadmap throughout the design process. Top Secret’s design pillars are mentioned on the Kickstarter page but I wanted to delve a little bit deeper. Why were they chosen, and how will the inform the final design?
Investigations are unpredictable, personal, even creative. An detective can’t investigate without autonomy. This is why non-linearity is a core pillar of Top Secret, players have to be free to go where the evidence takes them.
It seems odd that a story could be revealed by a disordered narrative, but Her Story, a psychological study centred around a murder investigation, shows how this can work. A key inspiration for Top Secret, this successful indie game allows you to explore the evidence surrounding the case in any order. The result? A compelling experience unique to each player.
Related to non-linearity is the idea of width over depth. What do I mean by this?
You can think of interactive fiction as a tree with one starting point (the trunk) and many branches. Narrative branches represent possible player choices. Width describes the extent of the branching. Depth describes how tall the tree is, how many levels there are. This is a gross simplification, but works for now.
Some games are deep and narrow, with few meaningful choices but lots of content. Some are wide, with many choices to make and multiple branching paths. Both depth and width add content to the game, but width is more expensive to produce as it results in an exponential content explosion.
I want Top Secret to be a wide game. Even at the expense of depth. I want your choices to be significant and meaningful. Limited and transparent choices don’t result in eureka moments!
Many games loudly signpost the consequences of player choices. This is good for gameplay; transparency allows players to strategize. But predictability can render a narrative dull. Solution? Making choice consequences more opaque. Players are now free to make the decisions they want to make, rather than the most ‘optimal’ ones.
In Top Secret choices will have significant consequences, but not necessarily immediate or expected ones.
You don’t have to be super smart or a tech wizard to play Top Secret but you will need to pay attention. You’ll need to keep track of evidence and formulate plans. To be inquisitive and explore, and ready to learn!
This is a good thing.
A key part of the game is to teach the player about surveillance, and how to protect yourself from it. Encryption, infosec, opsec. You’ll learn a little about all these things.
Play a game and level up your real life skills. Result!

I’m very excited to announce that Failbetter Games is going to incubate Top Secret! I’ll be working in their offices and getting support from them throughout development. In fact I’m writing this from their office right now.
Failbetter are a London-based games studio best known for the critically acclaimed Sunless Sea and Fallen London. As well as being genuinely nice people, they are experts in game writing and I can’t think of a better place to be developing Top Secret.
You can find out a bit more in their blog post about incubating Top Secret.
What does this mean for you?
- I’ll be getting constant feedback from experts in writing and community management to improve the game
- I won’t have to pay for office space so more money from the Kickstarter will go directly into the game
So what’s the catch? Amazingly there isn’t one. Failbetter are doing this because they want to help out new indie devs, and learn from us as we learn from them. Failbetter won’t own any of the IP, and don’t have any control over the development of Top Secret. Of course I’ll still be listening very closely to their advice and feedback because frankly, I’d be mad not to.
In short, this is good news all round for Top Secret!
James
A comment on CNET regarding Top Secret recently caught my attention. It’s worth quoting in full:
“This sounds like an interesting concept, but I’d be afraid to play a game like this using real email. How many gamers playing this are going to be flagged as terrorists or spies by the NSA? How many are going to be placed on the no fly list, and how many will be investigated/arrested as a result of this game? Something like this has the potential to screw someone’s life up for real.
It’s all fun and games until someone gets placed on the terrorist watch list…”
Sensational hyperbole, or valid concern? Can you really be added to a terrorist watchlist for playing a video game?

Last year The Intercept released The March 2013 Watchlisting Guidance. A ponderous 166 page document full of legalese securocrat speak, it does nevertheless shine some light on the watchlisting process. In particular it attempts to define what ‘terrorism’ is, and the criteria required for a suspect to be added to the various watchlists currently maintained by US government departments. The examples given for ‘terrorist activities’ are sensible, including use of chemical or biological weapons, destruction of aircraft, and kidnapping the president. ‘Terrorism’ itself is described as involving ‘violent acts or acts dangerous to human life, property, or infrastructure’ which ‘appear to be intended to intimidate or coerce a civilian population’ or ‘to influence the policy of a government by intimidation or coercion’. Terms such as ‘coerce’, ‘intimidate’ and ‘dangerous to’ can be misinterpreted or stretched, but overall the definition seems quite reasonable and well-thought out. Certainly video game playing would not qualify. Case closed? Not quite.
The Intercept also revealed that the number of watchlisted individuals, as of 2014, was over 680,000. This seems high given the rather narrow definition above. How do we explain this discrepancy?
Firstly the level of evidence required to be watchlisted is quite low. Whereas US courts use the ‘reasonable doubt’ threshold, and warrants require ‘probable cause’, watchlisting requires only ‘reasonable suspicion’. This is the same standard for a police officer to briefly stop you on the street, but not enough for a full search. It has been suggested that even an uncorroborated social media post may be enough evidence to watchlist an individual.
Secondly, you need not be actively planning anything yourself to be added, only to be associated with an individual on the watchlist. What does ‘associated’ mean? If you’re a relative, friend, have communicated with, or offer financial or material support in any way to a suspected terrorist, you can be added to the list without any suspicion. This rule is behind the belief that just by being on someone’s phone, or in the same internet chat room as them, you too could be added to the watchlist.
Ultimately how the guidance is interpreted comes down to the political climate of the time, oversight mechanisms in place, and available resources. The hundredfold increase in the number of watchlisted individuals post 9/11 is as much due to expanded intelligence budgets as with policy change.
Despite this, you can rest easy. You won’t get added to a watchlist for playing Top Secret any more so than for watching Citizenfour, or reading about the Snowden leaks in The Guardian, or New York Times.
The more interesting point is the fact that people are worried about this in the first place.
![]()
Imagine a cylindrical prison where every inmate is within line-of-sight to a central pillar. You can see out from the pillar but not into it. Prisoners never know when they are being watched so must constantly act as if they are under surveillance.
This concept (known as the Panopticon), was devised by Jeremy Bentham in the 18th century as a means of controlling many prisoners with few guards. The key insight being that the mere possibility of surveillance is enough to change behaviour.
Most surveillance is covert and clandestine, but a panopticon derives its power from the awareness of its subjects. In fact, belief in the existence of it is the sole requirement. Neither intent, nor reality are necessary for control. This contrasts with more obviously intentioned mechanisms such as China’s recent credit score system (https://www.aclu.org/blog/free-future/chinas-nightmarish-citizen-scores-are-warning-americans).
Today, technology allows us to construct panopticons with ease. A single CCTV camera in each cell would suffice, or interception of satellite communications, or wiretaps on global fibre optic cables…
Post-Snowden we are all Bentham’s prisoners.
For those in the creative or research industries this can be keenly felt. I’ve spent a lot of time researching the NSA and their surveillance programs whilst developing Top Secret. Perversely, the more you know, the stronger the controlling effect. With every new fact and detail, the panopticon gains strength.
People I meet jokingly suggest I must be on a watchlist. Humour tinged with the tiniest sliver of doubt. Others joke that they won’t play the game because they’ll be added to one. We like to believe that our behaviour isn’t affected, the panopticon has no hold over us, but there remains an insidious fear that our self-censorship is inescapable and manifest.
Should I google that word, or visit that site? Or use that encryption method? Or play that game?
Maybe not.
One Kickstarter backer messaged me to ask how they could find out more about the Snowden leaks and I thought this would be a good time to provide a few pointers.

Firstly, if you haven’t seen it yet, I highly recommend the Oscar-winning documentary Citizenfour. Shot ‘in the room’ as the leaks took place, this is not only an important historical record, but also a great film in its own right.
Directed by Laura Poitras, the majority takes place in Hong Kong where the protagonists are holed up in a claustrophobic hotel room. Snowden knows he could be arrested at any moment, and the tension is incredible. It’s the kind of story which you might think is a John Le Carré novel if you didn’t know it was real.
Poitras is a fearless journalists. Stopped for years at airports after being put on a US government watchlist, she was perfectly placed to understand the importance of the story. She’s also a great film-maker. An advocate of a stripped back, observational style, she eshews complex camera work and staged interviews to let the raw footage speak for itself.
Citizenfour is a huge inspiration for me. It’s an unusual mix of journalism and entertainment which is exactly what I want with Top Secret. Emails sent between Poitras and Snowden will be a key component of the game.
TLDR: Go watch Citizenfour, you won’t regret it!

Penned by Glenn Greenwald (another key character in the leaks), No Place to Hide covers similar ground to Citizenfour, but also explores the contents of the leaks. If you’ve heard of PRISM, XKEYSCORE, and BOUNDLESS INFORMANT, but are not sure what they are, this is the book for you.
The great thing about this book and Citizenfour is that they are made by people who were actually there. This is all first-hand journalism and it shows.

Long before Snowden leaked any documents, a hard-nosed, inquisitive journalist called James Bamford was writing about the most secretive of US intelligence agencies in extraordinary detail.
covers the rise of the NSA from 9/11 onwards and reveals the incredible scaling-up of the surveillance infrastructure in the wake of the attacks. Lots of things proven by the Snowden leaks were mentioned here first and if this book shows us anything, it is that hard evidence matters. James Bamford had numerous sources and impressive rigour, but it wasn’t until raw documents were leaked that people sat up and noticed.
This book is brilliant if you’re a security geek like me. There’s a tonne of intricate detail, and great securocrat anecdotes. Bamford shines a light on the revolving door between the public and private surveillance sector, and the illegal warrantless wiretapping program instigated by president Bush.
This is a heavier read than the other books mentioned here, but you won’t find this information anywhere else. A must read.

This is probably the most well-known (and successful) book here but is the one I would recommend the least. That’s not to say it isn’t engaging (because it is) but it lacks the first-hand authenticity of Citizenfour/No Place to Hide, and the rich detail of The Shadow Factory. Much of the content covered in this book is presented better elsewhere.
What this book does offer is a deeper look at Edward Snowden himself, from his childhood, to his employment in the US army, CIA, and eventually NSA. Snowden has lead an unusual life and knowing the facts does help put the leaks into context.
So why the reservations?
When reading , you can’t escape the feeling that the book was rushed out to capitalise on the leaks. Some passages seem hurried, and others lack detail. There’s also a lot of second-hand journalism. Luke Harding (the author) has never met Snowden.
In summary, it’s worth a read, but not essential.
Since covering the initial leaks, both Greenwald and Poitras helped set up The Intercept. This is definitely the news site of choice for surveillance issues and has begun covering world events with similar detail and insight. Greenwald’s acerbic prose skewers Washington hypocrisy with ease and while you might not agree with everything he says, you can’t ignore him.
James

That’s right! The Kickstarter is now live HERE!
Momentum is crucial to Kickstarters so if you’re thinking of backing Top Secret please go to the launch page right now and pledge!
You can also help by tweeting about the Kickstarter, and posting/sharing on Facebook, reddit, tumblr, instagram. There are share buttons at the bottom of this post to make it easy!
The demo is also live here.
Oh and if you want to experience the ups and downs of launching a Kickstarter then follow my for updates.
Thank you so much!
James
Here’s the first teaser trailer for Top Secret. Enjoy!
That’s right! The Top Secret Kickstarter is only 2 weeks away!
Make a note in your diary. Set an alarm. Cancel your plans. Be hyped. Don’t get any sleep. Oh wait, that’s my todo list for the next fortnight…
On a more serious note, I’m really excited (and terrified!) about doing this, and it’s only going to succeed with your help. Every share, tweet, and friend you tell is a gift that will help Top Secret become reality.
Keep an eye out for more updates soon, and remember, remember the 23rd of September.
James

People like shiny pictures and even text-only games need some art. Creating promo assets is not, however, one of my strengths. So I entrusted the task to my super talented ex-colleague from Turbulenz .
Here’s a sneak peek!

One of the contradictions of Top Secret is that it’s a game about the dangers of surveillance, in which your play is itself subject to surveillance. Every email you send whilst playing can be intercepted and read by the NSA or GCHQ. What if there was a way to send messages in the game securely? Enter PGP.
“PGP empowers people to take their privacy into their own hands. There has been a growing social need for it. That’s why I wrote it.”
- Philip R. Zimmermann
PGP is the method used by Snowden and others to protect the contents of their communications. It’s a form of end-to-end encryption where only the receiver can decrypt the message. It’s been around for over 20 years and is still used by activists (and spies) all around the world. As far as we know, it’s one of the few encryption methods the NSA can’t break.
So how does it work?
Imagine you have an unbreakable, unpickable padlock to which only you have the key. You give the padlock to a friend. They can now put a message in an unbreakable box, lock it with the padlock and send it to you knowing that only you can open the padlock to see the message. It doesn’t matter if the box is intercepted en-route because only you have the key to open it. Even your friend can’t open the box once it’s locked.
Your clever friend also has an unbreakable padlock with their own (different) key so you can send them messages the same way. You can now communicate securely (as long as you keep your keys private. Hooray!
In real life, unbreakable boxes and unpickable padlocks don’t exists, but they do digitally (or close enough). With PGP, instead of a padlock, you have a ‘public key’. It looks something like this:
-----BEGIN PGP PUBLIC KEY BLOCK----- xm0EVWcuBgEDALKVn7OEvu5VYvHPOcCbA/fuZA7vwLb12dLzUksPAm0w54flpgaN RkMNlEqIKfjSjlZ2pT5u+rZsLy1rcq4bgRNiQCfzga74xyz7MO98rdDfyOKNOlxt 8h3AWUcKRzoAowARAQABzSpmbkNvbnRhY3QuY29tIEZvcm0gPG5vcmVwbHlAZm5j b250YWN0LmNvbT7CjQQTAQoAFwUCVWcuBgIbLwMLCQcDFQoIAh4BAheAAAoJEKti Z87L+YgvhuADAJVCqM3YNja8ro3CtsMQ7xQp97sCuSf+WB/O5Oku5WUFN5LeT+k4 +r9MxaZuUA+wZioloJ1ncA3cqbbLENd+Fs7TA+XHiUPVXP0QOj03c60DDxOQauVG E/vKUlm3toYMws49BFVnLgYBAYDbGunnlWZw26RALWxRTuTKgnjT7ck7NjGIsgB5 jOOvAXocZVPm+5XDSJ6sey7ZlhUAEQEAAcLAEwQYAQoADwUCVWcuBgUJDwmcAAIb LgBYCRCrYmfOy/mIL00gBBkBCgAGBQJVZy4GAAoJENP5vF/vC7+jR44Bfju/0Vk2 WI6ySqQx+gXorh7Kg7Op3diVK3kC0b7U7JS8mS6WbE1+HopQKG5eFjIuIkPBAwCK RtnnoZHtj/08VorTktapJZjpgWQheqHuHPbqI+pQ0VOZvNi/hA5jm248lZA3sWpw e6YqHwZ5QvpDpmmuUwG0ydk+8eOV8aOV/WRHWe4rUBqRyCzmD9KbWDyoorRftyfO PQRVZy4GAQGAvPtA/VhdQYXHzv9/FQvwy5zlDvhQUlMfi8ok5WrC58g3m5zVQyMZ DJmjTMBqTep7ABEBAAHCwBMEGAEKAA8FAlVnLgYFCQ8JnAACGy4AWAkQq2Jnzsv5 iC9NIAQZAQoABgUCVWcuBgAKCRAdgsllJW7g8IlZAYCbZW+Xq5IziBDqbkJYLvmr svoiynwYKIUrzA1R5jjKKLj5i0zWBN2CNwizvfZOY58PfwL/bumDIUJvwHSGs+2c 6gW1OuqZhAEJnh/GPtDJspnCu3QEznxrzw/FtACMHWjU0Zz88e6lhz5L90cG6s9T Q3FcstH2jqMcTOKlHsa1jTmiCyY4rHzRRX4CtwYEPq5qv1Vp =qiac -----END PGP PUBLIC KEY BLOCK-----
Your friends can lock (encrypt) messages to you with a copy of your public key. Then, when you receive a message, you can unlock (decrypt) it with your private key.
Just like with the padlock-key example, this only works if no-one else has a copy of your private key, and your friends only lock/encrypt using your padlock/public key.
When you sign up for the game, you can now add your public key. Each character in the game has their own public key, so you can receive and send encrypted messages to them using PGP.
If this all sounds a bit complicated, don’t worry! You can still play using regular, unencrypted emails - PGP is completely optional.
For me though, PGP gives the most authentic and immersive experience - there’s something thrilling about sending a receiving real secret messages.
Now you can experience that feeling playing Top Secret.
Only a day after an appeal court in the US ruled an NSA surveillance program illegal, the UK has struck a blow to opponents of mass surveillance worldwide. For those of us who believe in digital rights, this election could not have gone worse.
It’s a disaster, and let me explain why.

Under the coalition, the Conservatives were desperate to pass the Communications Data Bill (aka the Snooper’s Charter). Luckily their coalition partners, the Liberal Democrats, were wary of the idea and the bill was put on the backburner.
Until today.
The Home Secretary Theresa May has confirmed that the new Tory majority government will revive the Snooper’s Charter and you can bet they’ll try and pass it into law as soon as they can.
The draft bill would dramatically expand the scale of mass surveillance in the UK. It forces every mobile phone and internet company to store data (but not content) on every single message you write, site you visit, social media activity you carry out, voice calls you make, email you send, and make that data accessible to the police and security services without a warrant or judicial oversight.
It would allow the government to force the Royal Mail to record the detail of every postcard, letter, and parcel sent (delivery/return address, names etc) throughout the UK.
It would allow the security services to install ‘black boxes’ at every ISP to carry out man-in-the-middle attacks on all your web traffic.
Imagine you’re a whistleblower, a leaker, a journalist, or a human rights lawyer, what hope will you have to communicate in private when all your movements, messages, and calls are stored and accessible almost in real-time?
I know this all sounds a bit 1984, but it is real and it’s very possible this will become law so we need to do something about it.
“If we do not act, we risk sleepwalking into a society in which crime can no longer be investigated and terrorists can plot their murderous schemes undisrupted.”
- Theresa May
At a recent Q&A Alan Rusbridger (Guardian editor-in-chief) had some rather striking thoughts. He has spoken to many senior government officials about surveillance and the Snowden leaks, and said they find it impossible to think rationally about these issues.
They are petrified of being seen as weak on terrorism. They live in fear that some new attack will happen under their watch. So when representatives from GCHQ come knocking on their door asking for more powers, politicians fall over themselves to acquiesce.
It doesn’t help that the average MP grew up when the internet didn’t exist, and barely knows what Facebook is.
I still believe that enough MPs can be persuaded to vote against the bill, but it will take a huge effort to get even a small number to go against the whip.
And if MPs don’t listen, what can we do?
“Trust the math. Encryption is your friend. Use it well, and do your best to ensure that nothing can compromise it. That’s how you can remain secure even in the face of the NSA.”
- Bruce Schneier
Use services with strong end-to-end encryption. The market for secure communications services has flourished post-Snowden, and apps such as Signal and TextSecure are great ways to fight back against mass surveillance.
Support organisations such as the Open Rights Group (UK) or EFF/ACLU (US) who work tirelessly to protect privacy and digital rights.
And don’t give up.
As the recent court ruling in the US has shown, there is still hope. People and companies are waking up to the importance of privacy and encryption, and there are still multiple legal cases going through the courts on both sides of the Atlantic.
“I do not want to live in a world where everything I do and say is recorded. That is not something I am willing to support or live under.”
- Edward Snowden
This battle is far from over.
AKA How to create a Kickstarter video when your game has no graphics and you’re an awkward penguin.
I always knew the video was going to be a tough ask for me. I had no fancy visuals to fall back on, and I have a strong aversion to cameras. Unfortunately, I had a nagging belief that backers might actually want to see my face and get to know me a bit before pledging so I decided to go for a fairly simple, straight-to-camera pitch.
Naturally, I made a few mistakes and learnt some things along the way.
I had a script for my initial filming and it was a big mistake. My logic went like this:
- I need to make sure I include points X, Y, and Z for the game to make sense
- I need to do this within two minutes
- A tight script will allow me to do this in a slick, efficient way
Wrong!
Unless you’re a gifted actor, a memorised script always comes across as forced, unnatural, and worse, dull. I didn’t even intend to use the script verbatim, but my fickle mind kept falling into the same prepared phrases I’d laboured over in advance.
In the end, the footage was so bad, I had to start filming from scratch.
Bullet points are the way to go.
The abilities to create and to pitch don’t always come hand in hand. Many brilliant game developers are living proof of this. If you’re not a natural in front of a camera, the most important thing is to film in an environment where you are totally comfortable.
I learnt this lesson the hard way.
Initially, I hired a professional to film my pitch. She was really lovely and had all the gear for great lighting and sound. Unfortunately the giant camera, lights, and a stranger staring at my face caused me to tense up. I was robotic, and none of my enthusiasm and excitement for the game came across. In the end, I couldn’t use any of the footage and was out of pocket.
My solution was to film in an empty house with a laptop webcam. This way I could be relaxed and natural. I’m still not going to win any presenting awards, but I’m much happier with how it turned out.
Ok, so you have your bullet points, you feel comfortable and you’re ready to go. Just film each bullet point twenty times and choose the best when editing right?
Wrong.
Unless you’re experienced at filming, you need to review the footage as you film it. Talking about the same point multiple times can quickly sap your energy and result in the same tired, scripted performance you were trying to avoid. Maybe your stressing or phrasing doesn’t work on camera and you don’t realise it? Maybe you’re using too much energy? Maybe too little? If you’re filming on location, or with a certain setup, you don’t want to have do retakes later!
Fewer takes with immediate reviewing of the footage will serve you better. You don’t want to have to go through thirty plus versions of everything in post production, trust me.
If your game does have sexy graphics and/or you are great at presenting, feel free to ignore everything I’ve said, and bask safe in the knowledge that your video will be infinitely better than mine.
But, if you’re in a similar boat as me, I hope you found my advice somewhat useful.
Thanks for reading.
James
PS. If you’re wondering how my final video turned out, you’ll have to wait for the Kickstarter! ;)
Recently there’s been a bit of a hubbub in the gaming press concerning unfulfilled promises and crowdfunding failures. This was kickstarted ahem by issues surrounding the Peter Molyneux project ‘Godus’ and culminated in the now infamous Rock Paper Shotgun interview which begins ‘Do you think that you’re a pathological liar?’. In that context, and given that I will be launching a Kickstarter campaign for Top Secret soon, I thought it would be a good moment to share my thoughts about crowdfunding risks.

Molyneux referred to the huge pressure to over-promise in order to secure funding during a crowdfunding campaign. With Kickstarter it’s all or nothing - you only get the money if you hit your target. For a struggling campaign with only a few days to go, there’s a big temptation to say whatever’s necessary to get those final pledges. Be wary of projects which promise new features mid-campaign. I won’t be doing this with Top Secret.
As well as overpromising, it’s tempting for devs to underestimate the money they need. The number of pledges made is often affected by how likely backers think a project will achieve its target (no-one wants to back a failing campaign). Allied to the ‘all-or-nothing’ mechanism, this creates a perverse incentive to deliberately set your funding goal lower than necessary in the hope that you will overshoot it. It’s fair to include an element of risk in your budget, but often the target asked for wouldn’t even cover the dev’s salaries under ideal circumstances.
Some risks are subtle - maybe the game doesn’t turn out to be quite as good as you hoped, maybe it wasn’t exactly how you imagined or goes in a direction you don’t like. Others are more predictable - perhaps the project is unexpectedly delayed, perhaps the project is cancelled.
All these things can, and do, happen.
In traditional investments, the investor gets something extra for taking on risk. With crowdfunding they often don’t. This isn’t necessarily a problem though. Risk can even be a reason to back an project. Kickstarter shouldn’t be used as a glorified shop-front or a marketing tool for well-worn ideas. It should be used to help innovative, challenging, and yes, even risky projects to completion which otherwise wouldn’t exist.
Ultimately, all these issues come back to one question: How much do you trust the project creators? Do you trust them not to over-promise, not to under-budget, not to be incompetent or deceive?
It’s a hard call to make.
This may all seem a bit of a downer but don’t forget that there are many brilliant and innovative projects which could only happen via crowdfunding.
Sometimes, as long as you know what’s involved, the risk can be worth the reward.
So how exactly do you play Top Secret?
The story is told via emails sent directly to your real inbox over the course of 2 weeks. Each character in the game has a unique email address and sends you messages which you open and read just like any other email.
You interact with the game by replying to those messages.
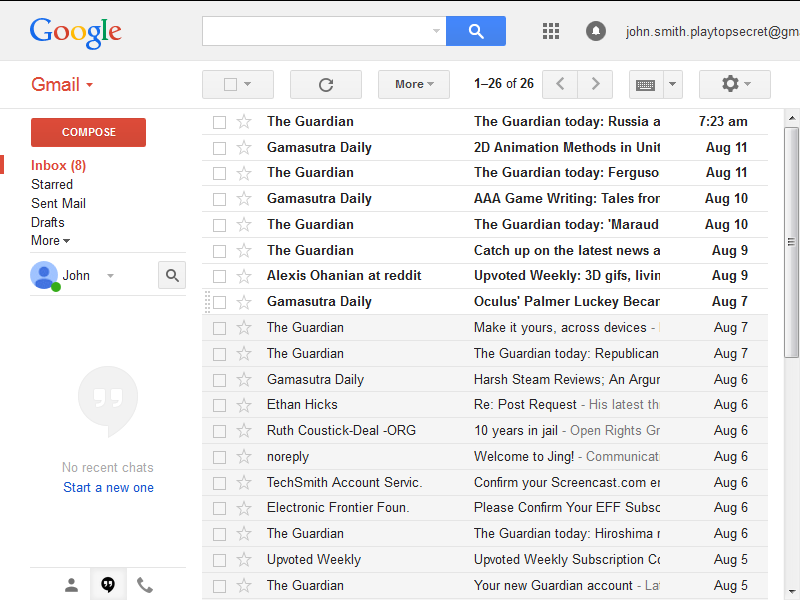
Messages which you can reply to are signified by options at the bottom of the email. For example, if the player was sent the message:
Who shall we look into next?
* Glenn Greenwald
* Micah Lee
The reply options here are ‘Glenn Greenwald’ and ‘Micah Lee’. The player can phrase their response however they like, but must include one of the reply options. E.g.
Hmm, let’s look at Glenn Greenwald first.
or
Micah Lee looks more suspicious to me. Let’s focus on him for now.
The game parses your message to detect which response you have chosen and continues accordingly.
If the player includes 0, or more than 1, valid reply options, the character they messaged will email back asking for clarification.
Simple, right?
No!
You will receive a small number of emails per day whilst playing the game. However, you can opt-in to more content by replying to emails. The more emails you reply to, the more emails you receive back.
To be clear, you WILL miss out on content if you don’t engage with the other characters in the game! However, the game will continue even if you don’t reply to most of the emails (although this will affect your relationships with colleagues and the plot).
No.
When starting the game you will specify your timezone, and all the messages are sent at the right times for you.
If something isn’t clear, send me an email or tweet and I’ll be happy to get back to you.
Thanks for reading.
James
I’ve been a bit coy about the project so far, but now it’s time to open up a bit and tell you what the game is, and importantly, how you play it.
Top Secret is an interactive fiction game about the NSA and Snowden leaks. It’s a game about secrets, encryption, privacy, and the ethics of surveillance.
It’s played in real time, over two weeks, by email.

You may be a bit confused at this point. So I’ll explain.
You (the player) will receive and reply to real emails from the characters in the game over the course of two weeks. You read and reply to them just like any other normal email you receive, directly from your inbox.
I’ll describe in more detail how this works soon, but for now, all you need to know is that to play the game, you only need an email address.
The game begins on Thursday 23rd May 2013. The Director of the NSA has learned that the Washington Post has received Top Secret documents and wants you to identify the source of the leaks.
Your team will be providing you with intel and surveillance reports on the targets you select. You’ll work together to a common goal and gain their trust.
What your colleagues don’t know, is that you’re also spying on them.
The Director believes there is a mole in the team and has tasked you with surveilling them to find out. How willing are you to pry into your own colleagues’ private lives? Will you protect your friends or betray them? It’s up to you.
There’s still a lot to be done. I plan to do a Kickstarter soon to raise funds to complete the game. And if you’re still confused about how Top Secret is played, don’t worry! I’ll be explaining the email mechanics in a lot more detail in the next blog post.
Thanks for reading.
James

I felt nervous and excited as the door closed behind me. The CEO looked up expectantly.
‘I’ve decided to leave’ I said.
If he was surprised he hid it well.
‘I’m going indie.’ I added.
And that was that.
As we shook hands I experienced a momentary crisis - I’d worked so hard to get a job in the video games industry and now I was giving it all up. Had made a terrible decision? I pushed the troublesome thought to the back of my mind.
A few months later I was experiencing a real crisis. Being an indie dev was meant to be fun and liberating, so why did it feel like such a chore? My initial ideas had seemed so exciting, now they felt tired and derivative. What was the point in being independent if I didn’t believe in my own game?
What was I really passionate about?
I thought back to the previous June when articles started appearing in the Guardian. They talked about security, surveillance, privacy and secrets - issues and ideas which had resonated with me from the very start. I had read every article, followed every twist and turn. I knew this was important. But most of the media here in the UK ignored the issue. It seemed like nothing had changed. Friends said they weren’t worried because they had ‘nothing to hide’.
Sometimes it seemed like I was alone.
But I had my answer. I knew I had to make a game about the Snowden leaks.
I had to make TOP SECRET.